
Cyber attacks on industrial network
Cyber attacks on industrial network
"Industrial IT Security will become increasingly important in the years to come. As Industry 4.0 and the Internet of Things (IoT) advance, systems and installations will be globally interconnected in the future. Given this, the risks of misuse will have to be re-assessed and new mechanisms developed to offer improved protection against malicious attacks."
Prof. Dr.-Ing. Axel Stepken
Chairman of the Board of Management, TÜV SÜD AG
Wednesday, January 13, 2016
TÜV SÜD Honeynet: Insights into cyber attacks attempts on industrial networks
Industry 4.0 presents powerful opportunities for companies in industrial segments to develop new competitive advantages. In order to harness these opportunities successfully, they must also be aware of the new challenges and take steps to minimise the risks that potentially threaten their business. Industrial IT security is one of the key topics that companies need to prioritise. As systems and processes become increasingly digitised and interconnected, potential entry points for cyber attacks grow; causing infrastructures and industrial facilities to become more vulnerable to sophisticated and professional cyber risks like espionage and sabotage.
In 2015, TÜV SÜD deployed a honeynet for a period of 8 months to investigate industrial cyber attacks and provide insights on the implications to companies.
“A honeynet is a decoy network designed to attract attacks, allowing detailed analysis of the access and attack methods to be conducted”, says Dr. Armin Pfoh, Vice President Strategy & Innovation at TÜV SÜD. In this project, TÜV SÜD simulated the network of a water works plant in a small German town. “To do so, we established a high-interaction honeynet, which combined real hard and software with a virtual environment”, explains Dr Pfoh. The experts worked with representatives from the utilities sector during development and implementation to ensure the systems and security measures were realistic and correspond to current industry norms.
The diagram below shows the "logic structure" of the honeynet.
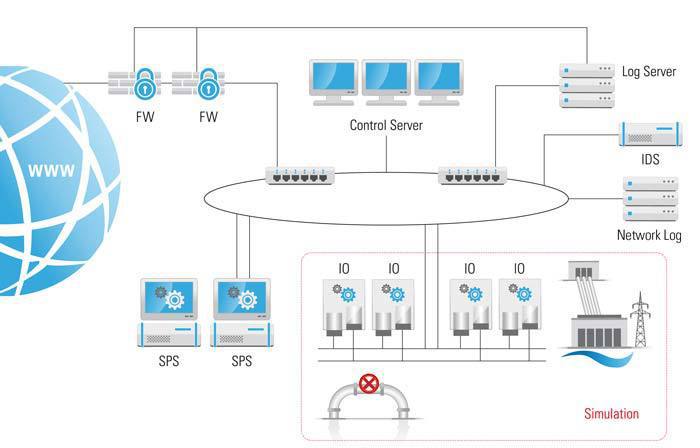
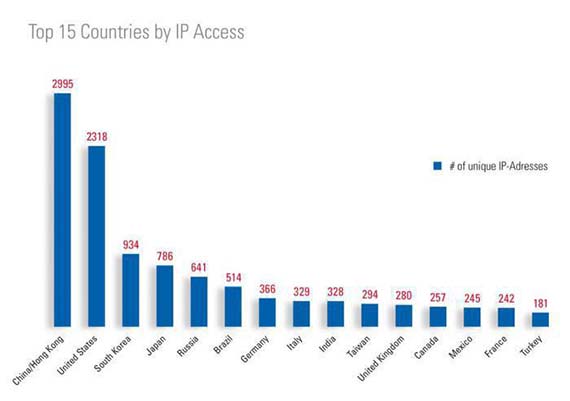
The first access attempt to the honeynet occurred as the network went live. Throughout the duration of the project, TÜV SÜD’s experts recorded over 60,000 access attempts from over 150 countries. “This proved that even relatively insignificant infrastructures are attracting attention and are being investigated on the Internet”, says Dr Thomas Störtkuhl, Senior Security Expert and Team Manager Industrial IT Security at TÜV SÜD.
Based on IP addresses, the top 3 countries in terms of access were from China, USA and South Korea. However, the IP address is not a reliable indicator of the actual origin of the attacker. In addition, some of the access attempts were made via hidden or spoofed IP addresses.
Interestingly it was also found that access was conducted not only via the standard protocols of office IT, but also via industrial protocols such as Modbus TCP or S7Comm. “While the number of access attempts via industrial protocols was clearly smaller, they too were launched from all over the world”, explains Dr Störtkuhl. Therefore he is certain that possible attackers probe for vulnerabilities in the security architecture of industrial control systems; through both general attacks on certain structures and devices as well as targeted attacks aimed at a pre-selected system.
The results from the honeynet project are a clear indication that infrastructure owners and industrial companies should not be complacent with industrial IT security. Small or little-known companies are being discovered and investigated as a result of the ongoing espionage campaigns on the Internet hence even companies that are not specifically targeted may become victims during a general attack.
Once companies come to the attention of possible attackers they remain vulnerable to targeted attacks in the future. This was indeed the case for TÜV SÜD’s honeynet - attempted attacks were subsequently launched through various protocols – one was a worldwide denial-of-service attack and two were targeted attempts via two different industrial protocols.
This exercise has highlighted that infrastructures and production facilities – even those of a relatively insignificant water works plant in a small German town – are continuously investigated. Such access attempts can lead to attacks that cause significant damages like the theft of business secrets and even sabotage of complete infrastructures that may result in the harming of people and the environment.
Therefore companies and owners of infrastructures should evaluate and adjust their security precautions to minimise these risks. Targeted monitoring is one of the prerequisites if companies are to assess their hazards realistically and develop effective protection measures. In addition, industrial protocols are known and utilised by possible attackers hence monitoring should go beyond standard office IT protocols and extended to industrial protocols.


How can we harness its potential while minimising the risks?
Learn more
Site Selector
Global
Americas
Asia
Europe
Middle East and Africa